Introduction
Cloud computing has completely changed the digital world, heralding in a time when massive volumes of information and applications are housed remotely, providing unrivalled flexibility and accessibility. A rising worry, however, has emerged in tandem with the fast spread of cloud technology: the susceptibility of cloud settings to a wide variety of security risks. In this article, it will explore the deep and complicated topic of “Cloud Vulnerabilities as well as Security.” Knowledge and mitigating the risks associated with storing, processing, and transmitting sensitive information in the cloud is becoming more important as organizations and consumers depend more and more on these services. The safeguarding of computing in the cloud is a complex environment that requires assignment help UK, rigorous examination since it is vulnerable to a wide variety of attacks. In an age when online stability is of fundamental significance, this article tries to examine the complexities of cloud security, investigate vulnerabilities, and look into the emerging tactics for protecting the cloud infrastructure.
Discussion
Cloud Architect
Software as a Service (SaaS)
SaaS architecture companies eliminate the requirement for end users to install software locally by delivering and maintaining software and other applications to organizations via the Internet (Haseeb et al., 2020). A wide range of devices and operating systems may use the same web interface to access SaaS apps.
Platform as a Service (PaaS)
In this cloud architecture, the service provider rents out a whole software stack, from servers to applications to middleware. Companies may use that foundation to launch their own software or services (Febriani & Purwaningtias, 2022). While the customer is in charge of software installation and configuration settings, the supplier of cloud services handles the networking, servers, and storage needed to host the application.
Infrastructure as a service (IaaS)
In this bare-bones type of cloud computing, a third-party provider takes the place of in-house servers, networks, and storage devices (Scheuner & Leitner, 2019). Organizations may control their software and apps and pay for just the resources they use.
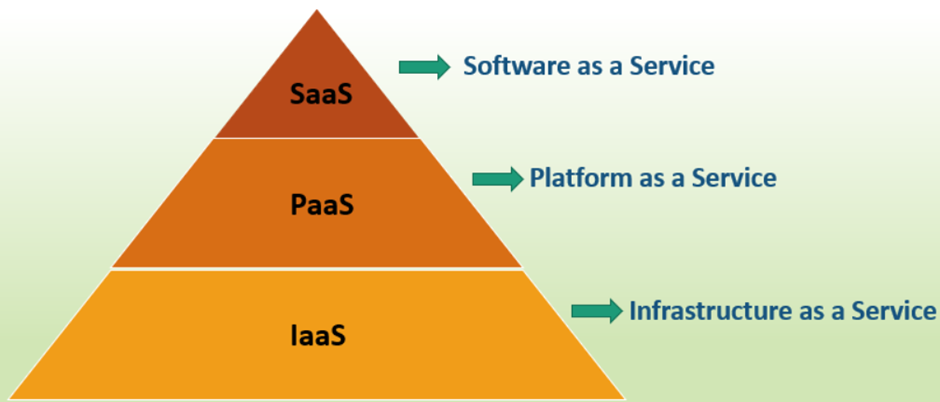
Figure 1: Various Cloud Services
(Source: educba, 2023)
Various Cloud Models
A variety of standard cloud architectural models exist, despite the fact that no 2 clouds are identical. They range from completely open to completely closed, hybrid, and even several cloud systems. Read on to see how they stack up:
Computing resources in a “public cloud architecture” belong to and are managed by the cloud services provider. Through the Internet, these assets are pooled and transferred among several renters (Kahn et al., 2022). Reduced overhead, simple scalability, and almost no upkeep is just a few of the benefits of moving to the public cloud.
A private cloud is one that is owned and operated by a single corporation, Make My Assignment UK, often inside that firm’s own physical data centre. Private clouds, on the other hand, might include a wide variety of servers and colocation facilities. Private cloud design is sometimes more costly than public cloud systems, but it provides more control over data safety and regulation measures.
A hybrid cloud architecture mixes the cost savings of public cloud operations with the privacy and security guarantees of private cloud storage (Achar, 2021). Hybrid clouds use both private and public cloud architectures to enable organizations to consolidate information technology assets and transfer workloads across environments based on IT along with information security needs.
A multi-cloud infrastructure is one that makes use of more than one public cloud provider. One of the benefits of a multi-cloud infrastructure is that it gives people more options when it comes to selecting and deploying cloud services to meet people are unique business needs (Zhu et al., 2021). Another benefit is a decreased risk of being “locked in” to using just one particular cloud service provider. Microservices-based containerized apps may also need a multi-cloud architecture to function properly if their constituent services are distributed over more than one cloud.
Data Security in Cloud
Data Confidentiality: Only authorized users or systems are able to access or make changes to the data. The information belonging to the organization must be protected at all costs.
Data Fidelity: In other words, the information may be relied upon to be true. The goal is to put in place procedures and safeguards that stop information from being altered or lost.
Data Access: While it’s important to prevent unauthorized access, organizations also need to make sure that authorized users and systems can access the data they need (Moustafa, 2021). People will be responsible for maintaining a high level of availability and keeping all connected hardware in tip-top shape.
Figure 2: Cloud Architect Skills
(Source: techtarget, n.d)
Challenges of Cloud Architect
Misconfiguration
In order to cut down on expenses without sacrificing convenience, more people are turning to cloud computing. If the cloud services are set up properly, though, the company won’t have to worry about security risks (Nguyen et al., 2020). Users’ failure to take proper precautions while securing their cloud-based data and apps is the biggest security risk in the cloud.
Contraband Entry
One of the biggest problems with cloud security is unauthorized access to data. While the cloud offers organizations a handy method to store and gain access to data, it also leaves that data susceptible to cyber-attacks. Malware, hacking, and other malicious activities are all examples of cloud security breaches. Companies need to restrict access to sensitive information to prevent these kinds of breaches.
Account Takeovers
One of the most prevalent attacks against cloud security is the theft of user credentials. The possibility of having people are accounts compromised rises when people use cloud-based programs and services (Hassan et al., 2020). Therefore, Case Study Writing Service In UK, in order to maintain their privacy in the cloud, users must take extra precautions to safeguard their login credentials and other sensitive data.
Lack of Exposure
Cloud computing has simplified online data access and storage for enterprises, but this benefit is not without its drawbacks. Therefore, it is essential for businesses to take precautions against data breaches and theft. However, because of its dependence on distant servers, cloud computing also presents security risks.
Confidential Information
When it comes to the cloud, confidentiality, and privacy of information are two of the most important concerns. Businesses using cloud computing are concerned about keeping their data safe since employees may potentially access it from just about anywhere. Since businesses cannot choose who sees their records, it is their responsibility to restrict access to just those who need it.
Data Sharing with Third Parties
One of the biggest concerns when it comes to cloud security for organizations is the sharing of data with other parties (Wang et al., 2022). This problem occurs when a company must exchange information with service providers it has not thoroughly investigated and authorized. Furthermore, it will help in maintaining the privacy and integrity of critical information.
Acceptance of Law and Regulation
The cloud is a useful resource that may save expenses and boost productivity for businesses of all sizes. However, in order to safeguard information and guarantee conformity with legal as well as regulatory standards, new security concerns arise in the realm of cloud computing.
Resources Provided by an Untrusted Source
The term “third-party resources” refers to anything not directly associated with the cloud service provider. Potential security flaws in these sites might provide third parties access to information.
Recommendations
- Keeping the operating system and software up-to-date, performing regular security audits, using strong passwords, and using two-factor authentication are all important ways to protect against cybercriminals.
- While cloud computing raises the possibility of cyberattacks, businesses that pay close attention to their safety precautions might gain an advantage in the current business climate (Alam, 2020).
- In order to establish roles in different deployment scenarios, leading cloud service and platform providers like AWS as well as Microsoft Azure offer documentation. Enterprises should verify compliance with these basic security guidelines when selecting cloud suppliers in order to reduce the likelihood of misunderstandings and inadequate security measures or undetected incidents.
- If the service has security issues, people should work to address them by enhancing their own security measures. Some examples of this involve encryption, permissions, and oversight.
Conclusion
It can be concluded that cloud computing has revolutionized the digital world by making possible the remote storage of vast amounts of data and the delivery of previously inaccessible applications. SaaS programs often include a web interface that can be accessed from a variety of devices and operating systems. The cloud service provider takes care of the hardware, including the servers and storage, while the client is responsible for installing and configuring the software. These assets are shared among numerous tenants via online transactions. There are several advantages to using the public cloud, including lower costs, easier scalability, and nearly no maintenance. If the services that make up the microservices in a containerized system are spread out over many clouds, the app may also need a multi-cloud architecture. The largest security risk in the cloud is users not taking enough measures to secure their cloud-based data and applications. Top cloud service and platform providers like Amazon Web Services and Microsoft Azure both include docs that can be used to determine responsibilities across a variety of deployment models.
Reference
Achar, S. (2021). An Overview of Environmental Scalability and Security in Hybrid Cloud Infrastructure Designs. Asia Pacific Journal of Energy and Environment, 8(2), 39-46. Retrieved from: https://www.researchgate.net/profile/Sandesh-Achar/publication/365013376_An_Overview_of_Environmental_Scalability_and_Security_in_Hybrid_Cloud_Infrastructure_Designs/links/636327a92f4bca7fd028ec86/An-Overview-of-Environmental-Scalability-and-Security-in-Hybrid-Cloud-Infrastructure-Designs.pdf [Retrieved on: 16.09.2023]
Alam, T. (2020). Cloud Computing and its role in the Information Technology. IAIC Transactions on Sustainable Digital Innovation (ITSDI), 1(2), 108-115. Retrieved from: https://www.researchgate.net/profile/Sourav-Kunal/publication/333162093_An_overview_of_cloud-fog_computing_Architectures_applications_with_security_challenges/links/5d67850a92851c70c4c65a06/An-overview-of-cloud-fog-computing-Architectures-applications-with-security-challenges.pdf [Retrieved on: 16.09.2023]
Febriani, S., & Purwaningtias, F. (2022). Implementasi Platform As A Service (PAAS) Pada Aplikasi Getfix Berbasis Cloud Computing. SAINS DAN INFORMATIKA: RESEARCH OF SCIENCE AND INFORMATIC, 8(2), 86-95. Retrieved from: http://publikasi.lldikti10.id/index.php/jsi/article/download/1653/822 [Retrieved on: 16.09.2023]
Haseeb, K., Almogren, A., Ud Din, I., Islam, N., & Altameem, A. (2020). SASC: Secure and authentication-based sensor cloud architecture for intelligent Internet of Things. Sensors, 20(9), 2468. Retrieved from: https://www.mdpi.com/1424-8220/20/9/2468/pdf [Retrieved on: 16.09.2023]
Hassan, W., Chou, T. S., Tamer, O., Pickard, J., Appiah-Kubi, P., & Pagliari, L. (2020). Cloud computing survey on services, enhancements and challenges in the era of machine learning and data science. International Journal of Informatics and Communication Technology (IJ-ICT), 9(2), 117-139. Retrieved from: https://pdfs.semanticscholar.org/e910/0c7519bb7bf9292484232e17b0835ca877cc.pdf [Retrieved on: 16.09.2023]
Kahn, M. G., Mui, J. Y., Ames, M. J., Yamsani, A. K., Pozdeyev, N., Rafaels, N., & Brooks, I. M. (2022). Migrating a research data warehouse to a public cloud: challenges and opportunities. Journal of the American Medical Informatics Association, 29(4), 592-600. Retrieved from: https://academic.oup.com/jamia/article/29/4/592/6468865 [Retrieved on: 16.09.2023]
Moustafa, N. (2021). A systemic IoT–fog–cloud architecture for big-data analytics and cyber security systems: A review of fog computing. Secure Edge Computing, 41-50. Retrieved from: https://arxiv.org/pdf/1906.01055
Nguyen, D. C., Pathirana, P. N., Ding, M., & Seneviratne, A. (2020). Integration of blockchain and cloud of things: Architecture, applications and challenges. IEEE Communications surveys & tutorials, 22(4), 2521-2549. Retrieved from: https://arxiv.org/pdf/1908.09058[Retrieved on: 16.09.2023]
Scheuner, J., & Leitner, P. (2019, March). Performance benchmarking of infrastructure-as-a-service (IaaS) clouds with Cloud WorkBench. In Companion of the 2019 ACM/SPEC International Conference on Performance Engineering (pp. 53-56). Retrieved from: https://research.spec.org/icpe_proceedings/2019/companion/p53.pdf [Retrieved on: 16.09.2023]
Wang, Z., Gupta, R., Han, K., Wang, H., Ganlath, A., Ammar, N., & Tiwari, P. (2022). Mobility digital twin: Concept, architecture, case study, and future challenges. IEEE Internet of Things Journal, 9(18), 17452-17467. Retrieved from: https://www.researchgate.net/profile/Ziran-Wang-6/publication/358970927_Mobility_Digital_Twin_Concept_Architecture_Case_Study_and_Future_Challenges/links/631b52ca873eca0c00751707/Mobility-Digital-Twin-Concept-Architecture-Case-Study-and-Future-Challenges.pdf [Retrieved on: 16.09.2023]
Zhu, Q. H., Tang, H., Huang, J. J., & Hou, Y. (2021). Task scheduling for multi-cloud computing subject to security and reliability constraints. IEEE/CAA Journal of Automatica Sinica, 8(4), 848-865. Retrieved from: https://www.academia.edu/download/66724665/Task_Scheduling_for_Multi_Cloud_Computing_Subject_to_Security_and_Reliability_Constraints.pdf [Retrieved on: 16.09.2023]

